 I’ve been busy lately assisting with a number of Office 365 migrations. Every single one is different and while many are straightforward, In some cases, you will find applications or devices that don’t support the requirements for connecting to Office 365 using TLS or SSL or they may not even work over standard ports such as 587. Working with one SMB recently, they had a critical Line of Business application that was written internally and can no longer be maintained by anyone in-house. They had identified a path forward however we still needed to keep the app running for around 6 months post migration to Office 365.
I’ve been busy lately assisting with a number of Office 365 migrations. Every single one is different and while many are straightforward, In some cases, you will find applications or devices that don’t support the requirements for connecting to Office 365 using TLS or SSL or they may not even work over standard ports such as 587. Working with one SMB recently, they had a critical Line of Business application that was written internally and can no longer be maintained by anyone in-house. They had identified a path forward however we still needed to keep the app running for around 6 months post migration to Office 365.
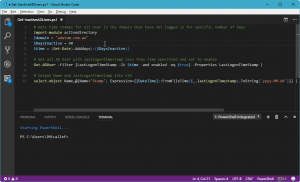
This is where stunnel, which is a TLS Proxy comes in handy. Grab the latest version from the stunnel website and install it. This little TLS/SSL proxy tool allows for us to listen for standard For our purposes we will install the Service instance so that it is always running whenever the server reboots. Once installed we can start building our configuration file. I’ve outlined a simple one below;
#Basic Configuration for Microsoft Office 365 POP3 and SMTP
output = stunnel-log.txt
debug=4
taskbar=yes
[POP3 Incoming]
client = yes
accept = 127.0.0.1:110
verifyChain = yes
CAfile = ca-certs.pem
connect = outlook.office365.com:995
[SMTP Outgoing]
client = yes
protocol = smtp
accept = 127.0.0.1:25
verifyChain = yes
CAfile = ca-certs.pem
connect = smtp.office365.com:587
This allows any application local on the same server as sTunnel to connect up to SMTP and POP3 on the standard ports then push this onto Office 365. We’re also pushing everything to a log file If you have issues with certificates the remove the verifyChain and CAFile lines which will prevent stunnel from attempting to verify the cert we receive from Office 365. If you are looking at doing IMAP or even need to do more with stunnel, see the example config files for more.