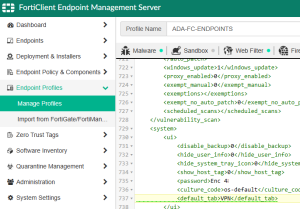
 It’s been a while, but I am working on deploying an updated version of FortiClient for and company which is managed via EMS and InTune. One thing that bugs me (and many) is by default, the client UI will load into the Zero Trust Telemetry tab and the option to change the Default tab will be greyed out for the end user when managed. There is no UI setting in EMS but you can easily set the Default Tab by using the XML editor for the specific profile under Endpoint Profiles > Manage Profiles, edit the Profile and then select XML Configuration. Once there, hit Edit and add the following line under the System and UI tags.
It’s been a while, but I am working on deploying an updated version of FortiClient for and company which is managed via EMS and InTune. One thing that bugs me (and many) is by default, the client UI will load into the Zero Trust Telemetry tab and the option to change the Default tab will be greyed out for the end user when managed. There is no UI setting in EMS but you can easily set the Default Tab by using the XML editor for the specific profile under Endpoint Profiles > Manage Profiles, edit the Profile and then select XML Configuration. Once there, hit Edit and add the following line under the System and UI tags.
<default_tab>VPN</default_tab>
You can also use any of the following values under the default_tab element to set the default tab accordingly.
AV: Antivirus WF: Parental Control/Web Filtering FW: Application Firewall VPN: Remote Access VULN: Vulnerability Scan
If you want to know what else you can configure via XML for the FortiClient via EMS, see the Fortinet FortiClient XML Guide here (or local mirror FortiClient_6.0.4_XML_Reference.pdf ).