So I recently came across an issue where some end users were getting prompted for their password when running a Windows Phone device (Android and Apple devices seem immune). The client had recently had an Office 365 hybrid configuration completed and where using ISA / TMG as a reverse proxy to authenticate to their local infrastructure for external users. Their move to a hybrid deployment required some changes to the way they had TMG setup (adding another web listener and re-configuring some rules).
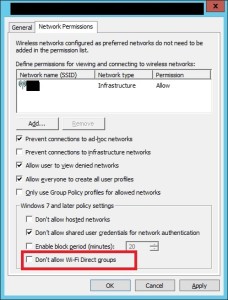
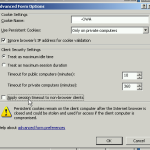
Judging from the password prompt, I quickly gathered that the issue was around a web listener, so opening up their one for Exchange, the listener used forms based authentication, so I went to the Forms tab and hit Advanced to see what options had been enabled or disabled. I could see that Apply session timeout to non-browser clients was enabled. After disabling this option and applying the changes, ActiveSync clients stopped prompting users for their passwords and the sessions remained active even after the timeout value expired.
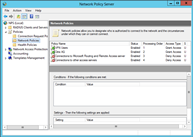 I was recently migrating an environment that ran two 2003 servers to two 2012 R2 servers. One of the challenges of migrations is ensuring there is as little disruption as possible, whether it is during business hours or not. This organization had a single RADIUS server controlling access to their 300+ users for Wireless and Remote Access.
I was recently migrating an environment that ran two 2003 servers to two 2012 R2 servers. One of the challenges of migrations is ensuring there is as little disruption as possible, whether it is during business hours or not. This organization had a single RADIUS server controlling access to their 300+ users for Wireless and Remote Access.