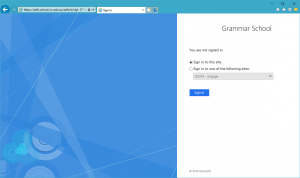
So usually one of the first things I do after initially setting up an AD FS environment (among others) is to test the Metadata (navigate to https://your.adfs.server/ federationmetadata/2007-06/federationmetadata.xml which should return valid XML) and sign-in functionality using the IdpInitiatedSignOn.aspx method. For Server 2012/2012 R2 this page enabled by default but if we navigate to this page on Server 2016 we get the following error;
An error occurred The resource you are trying to access is not available. Contact your administrator for more information.
The reason being is that this is disabled on Server 2016 and there is an extra step that needs to take place to enable it.
We can check to see the current status by issuuing the following command in a PowerShell window.
Get-AdfsProperties | fl
Scrolling down you’ll eventually see enableIdPInitiaedSignonPage which should currently be set to false, to change this issue the following command
Set-Adfsproperties -enableIdPInitiatedSignonPage $true
This enables the IdPSignonPage and allows us to test a login process for a SAML authentication supported application. Once this works I know I can safely begin to provision my applications to authenticate users against this AD FS server.