I was recently resurrecting an old demo environment in AWS which consisted of a few EC2 virtual machines, however upon trying to login, I quickly realised that the account password had expired and by default Windows Remote Desktop doesn’t have an ability to change passwords since you’re not presented with the logon screen. We didn’t have console access nor was there any other remote access like ConnectWise Control and since the only credential we had expired, we had to think outside the box.
I was recently resurrecting an old demo environment in AWS which consisted of a few EC2 virtual machines, however upon trying to login, I quickly realised that the account password had expired and by default Windows Remote Desktop doesn’t have an ability to change passwords since you’re not presented with the logon screen. We didn’t have console access nor was there any other remote access like ConnectWise Control and since the only credential we had expired, we had to think outside the box.
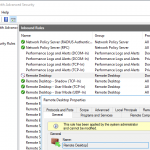
Luckily RDP can fall back to authentication via the logon screen and ask for login details after you connect. To achieve this, we firstly need to disable Network Level User Authentication or NLA on the remote machine, by tweaking the following registry key (this can also be done remotely).
Set-ItemProperty -Path 'HKLM:\System\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp' -Name "UserAuthentication" -Value 0
Once you’ve applied that setting one way or another (using something like Amazon SSM or Azure Virtual Machine Run Command) we then need to create an RDP file, open up Remote Desktop connection, enter the IP and hit Save As to create a file. Open it up in Notepad or your favorite text editor and add the following line to the end of the file
enablecredsspsupport:i:0
This disables the Credential Security Service Provider or CredSSP support and forces your connection to authenticate via the logon screen.
This setting is also handy for RDP farms or hosts that require interactive logins. Just remember that NLA needs to be turned off for this to work.
See Supported RDP properties with Remote Desktop Services on Microsoft Learn (RIP MSDN) for more info and supported parameters.