 So I was recently helping out a client clean up their Small Business Server environment, one thing they weren’t using was SharePoint, so we decided to remove it from their SBS 2008 server. The removal went smoothly, simply uninstalling SharePoint Services via Add/Remove control panel did the trick. But after a restart we found that clients were no longer connecting to their Wireless network, so I went did some troubleshooting and found that the NPS service hadn’t started since boot-up.
So I was recently helping out a client clean up their Small Business Server environment, one thing they weren’t using was SharePoint, so we decided to remove it from their SBS 2008 server. The removal went smoothly, simply uninstalling SharePoint Services via Add/Remove control panel did the trick. But after a restart we found that clients were no longer connecting to their Wireless network, so I went did some troubleshooting and found that the NPS service hadn’t started since boot-up.
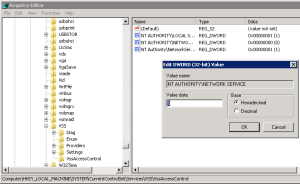
I then tried starting it up but got an error after trying to start the service with an unspecified error 0x80004005 which was very helpful. After some more digging around and Google-Fu I found that this had to do with permissions on a registry entry for VSS. The following key needed to be updated from the value 1 to 0.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\VSS\VssAccessControl
Make sure that the setting for NT AUTHORITY\NETWORK SERVICE is set to 1. If this is not and set to 0, change it to 1. Once you have changed the value you can restart or terminate any IAShost.exe that are running via task manager and then start up the NPS service.
This issue has been documented by Microsoft to occur if you remove SharePoint from SBS Server 2008, so just a heads up if you do and rely on NPS for authentication for things like Remote Access or Wireless.