So getting BitLocker enabled in an Active Directory environment is fairly painless and helps to get your end user devices more Secure. I’ll outline the steps you need to take to enable it as well as get the recovery keys stored in Active Directory. I’ll also dive into replicating this setup on Azure AD/Intune in a future post.
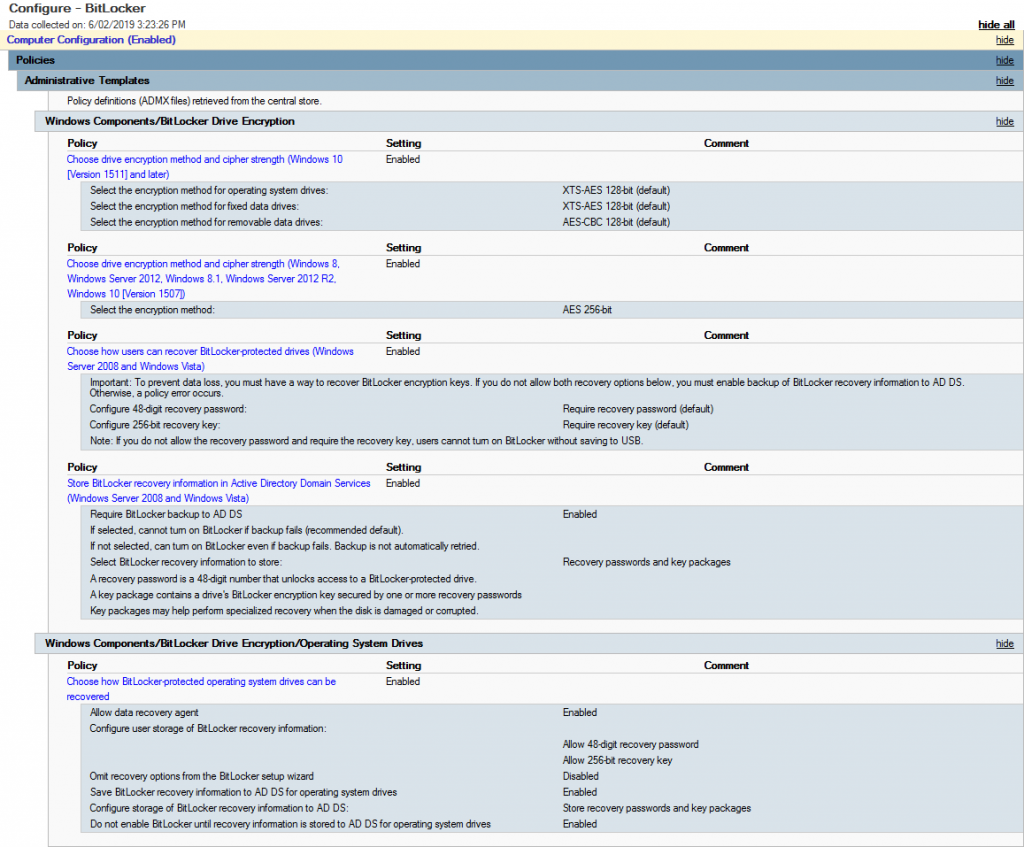
First thing is to create a new GPO (i.e. Configure – BitLocker) – Edit it and navigate to Policies > Administrative Templates > Windows Components > BitLocker Drive Encryption. Enable the following Options:
- Choose drive encryption method and cipher strength (Windows 10 Version 1511 and later)
- Choose drive encryption method and cipher strength (Server 2012, Win 8.1 etc…)
- Choose how users can recover BitLocker protected drives
- Store BitLocker recovery information in Active Directory Domain Services
Then go down one folder into Operating System Drives and enable the following:
- Choose how BitLocker protected operationg system drives can be recovered
Once you’ve set this all up, it should look something similar to the image below.
Now target the GPO to some machines and if you’re running 1809 (from what I’ve discovered so far) or later you’ll notice them start the BitLocker process to encrypt automatically. If not then you may need to check and ensure the TPM is enabled for the device (as we haven’t specified to encrypt devices without a TPM in this case).
What happens if you have already enabled BitLocker but now want to store the recovery keys in Active Directory? With this GPO set it will allow windows to write the recovery key to AD however we need to use the manage-bde utility, that is a command based utility that can be used to configure BitLocker
manage-bde -protectors -get c:
for /f "skip=4 tokens=2 delims=:" %%g in ('"manage-bde -protectors -get c:"') do set MyKey=%%g
echo %MyKey%
manage-bde -protectors -adbackup c: -id%MyKey%
I saved that as a batch file and ran that on the machines that had already been encrypted prior to rolling out the GPO. Once run, it escrows the key into Active Directory.
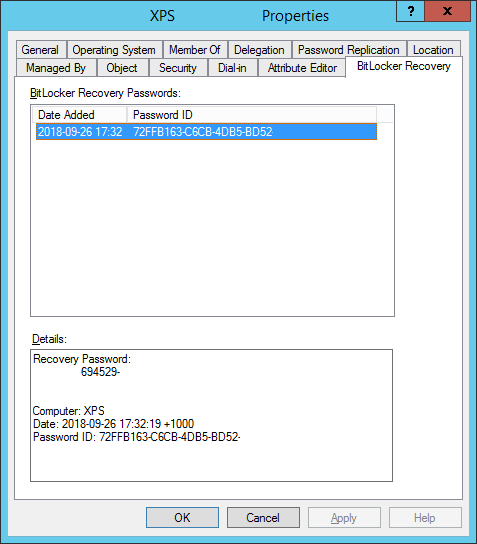
The last bit you will need to do so you can actually see the keys in the Properties tab or via the Search function in Active Directory Users and Computers, ensure that the BitLocker RSAT is enabled in Server Features and Roles.
Thanks – to clarify, if a C:\ is not encrypted and this GPO hits that machine, will it actually start encrypting the drive ?
It’s been hit and miss for me, if I’m joining the machine to the domain then this will apply and encrypt, but if I’m applying to an already joined machine, I’ve sometimes found we needed to start it manually.
Any machines already encrypted also won’t get their keys stored into AD automatically and you’ll need to run the manage-bde commands.
Now moving to InTune which presents its own challenges that I hope to share soon.
What do you mean by start it manually? I’m running into issues.
Perform drive encryption manually via Computer and right-click, manage BitLocker or using manage-bde command.
Hello again,
Thanks for your responses to my other questions. Sorry it posted twice. I’m a little impatient when I don’t see my post appear after submitting it.
So, if I take a computer that is domain joined, remove it from the domain, reboot it, then join it back to the domain should this apply the BitLocker policy?
Have you ever tried this?
Thanks!
I’m testing BitLocker GPO in my Domain, on Dell Latitudes 5400 running latest 2004 BitLocker starts encrypting OS drives automatically once I move them to the OU where BitLocker GPO is linked, but for some reason HP 840 G5 models ( I have about 500 of those) also running latest 2004 update I have to start the encryption manually. I noticed that TPM manufacturer is different on HP laptops, could this be the problem or something is missing in the pre-boot environment? Thanks
Can you be more specific on which features need to be installed on the DC itself?
I have enabled the BitLocker Drive Encryption Admin Utilities but want to know if I need to add the root level features, for the lack of a better term, BitLocker Drive Encryption and BitLocker Network Unlock?
Would these be required to unlock a drive before reimaging and redeploying a gently used laptop?
When we re-deploy a machine, the TPM is wiped and re-initialised and then our base image is applied and then handed to user for OOBE and final setup with InTune. Have not toyed with Network Unlock yet.
I was looking for a more detailed list of what Features need to be enabled on a DC for this to appear. Is it just the RSAT BitLocker tools, or do you need the two root BitLocker features as well? (BitLocker Drive Encryption and BitLocker Network Unlock)
Does this need to be installed on each DC that you want to see this tab in the properties page?
Thanks!
Hey, you just need the RSAT BitLocker to see the options appear in ADUC, it needs to be enabled on every DC that you want to see the tools on.
Hello John,
Sorry to be such a pest, but had a question about already domain joined computers. When I start BitLocker on one of these computers it still giving the end user the option to save or print the Key, even though I disabled both options in the GPO. Have you encountered that in your experience?
Thanks!